The OSI Model
The Open System
Interconnection (OSI) model was designed by the International Organization for
Standardization (ISO) as a model for helping different systems communicate. Its
important to note than back in the early days of networking, you would usually
be tied into a single vendor, since their systems could only communicate with
like systems, and multi-vendor networks made life a huge hassle. Back then, you
generally bought all IBM or all DEC equipment – once a vendor got that first
sale, they knew you were pretty much locked in long term. While good for the
vendor, this certainly handcuffed the customer in terms of their ability to make
choices based on what best met their needs. The OSI model was developed as an
architectural framework to allow different systems to communicate. It is not a
set of protocols or hard and fast rules. Instead, it acts as a set of guidelines
for how network communication should take place, which different sections of the
model outlining the roles and responsibilities of each section.
So why take this sectional or layered approach? Well, by making each layer
responsible for a different part of the communications process, we make it such
that a particular portion can be changed without affecting the other independent
parts. What starts off as data has to somehow be transmitted over the network,
meaning that information has to be added to account for the network technologies
in use, the addressing and routing of packets, the reliability of the transfer,
the actual way data is formatted, how the process is initiated, and so forth.
The OSI model actually maps to the packet generation process, and if you always
keep that in mind, you’ll be well on your way to truly understanding how network
communication takes place.
The OSI model has 7 layers, the 7 layers of the OSI model are numbered from
bottom to top as follows:
Layer 7 = Application Layer
Layer 6 = Presentation Layer
Layer 5 = Session Layer
Layer 4 = Transport Layer
Layer 3 = Network Layer
Layer 2 = Data Link Layer
Layer 1 = Physical Layer
It is important to know the order and names of the layers above. To make things
easy, I usually suggest creating a mnemonic to remember them. The phrase that I
originally learned was All People Seem To Need Data Processing (APSTNDP), with
each word representing a layer. In the beginning remembering the model can be
tricky, but once you truly understand it, you’ll never need to think about it
again.
Application Layer – The application layer is the top level of the OSI
model. Put simply, this is the layer where users actually interact with
applications that create the data that will be sent over the network. Imagine
you’re using a web browser. You type in www.cnn.com, and magically a whole lot
of data comes your way. The web browser doesn’t participate in the actual
obtaining of the data. It simple makes a request (this part is data) saying
‘hey, I need to view this certain web page’ the lower layers actually take care
of the rest of the request, and making sure that the data requested is actually
passed back to the web browser. What the browser is more specifically doing is
making a request that a web server will understand – an application on another
system. Examples of application-layer programs include web browsers, ftp
programs, telnet, email, and so forth. The user interacts with these directly.
Presentation Layer – Layer 6 of the OSI model is concerned with the
actual format that the data is presented in. It is important to note that
different systems have different ways of formatting data, and in order to ‘see’
things properly, the systems have to agree on a way that data will be displayed.
For example, data is often encoded using different schemes, such as ASCII,
EBCIDC or UNICODE. If one system formats data using a scheme that the other
doesn’t understand, you’re might just be staring a screen full of unrecognizable
characters, and that wouldn’t do you much good. This layer is home to a number
of data presentation standards that you might already be familiar with,
including JPG, GIF, and MPEG. However, this layer is also usually responsible
for data encryption and compression.
Session Layer – Layer 5 of the OSI model is one that people always seem
to have trouble with, mainly because in reality, protocols suites are often
developed such that they don’t map directly to the OSI model. The responsibility
of this layer is to create, manage, and terminate communication sessions between
systems. Think of the session layer as a coordinator of communication between
systems and you would be on the right track. A variety of protocols exist at the
session layer, including Remote Procedure Calls (RPCs), the Network File System
(NFS), SQL, and the AppleTalk Zone Information Protocol (ZIP).
Transport Layer – Layer 4 of the OSI model brings us to a place where the
actual roles and responsibilities start to get a little more concrete for
people. Its responsibilities include segmenting data that comes from the upper
layers, establishing a connection between end-to-end systems that defines the
parameters of the connection, and ensuring that data actually gets to its
destination in the correct order and error free. One way that it does this is by
requiring acknowledgements from the receiver for each packet transmitted.
Generally, if the packets sent don’t get to the destination, the sender will
never receive an acknowledgement, and will resend the data. At this layer,
systems also agree on how much data should be sent at a time, a process often
referred to as windowing, which will be discussed in a future article in more
detail. Beyond that, this layer also handles something called flow-control – a
process by which the receiving system can tell the sender to slow down, as it
may be receiving data more quickly that it can process it. Examples of protocols
found at this layer include TCP, UDP, and SPX.
Network Layer – Layer 3 of the OSI model is responsible for two key
functions – logical addressing and routing. This layer identifies systems
uniquely on our internetwork, and also handles how to get from one part of the
network to another. This is the layer where most of the network configuration
takes place, since protocols such as IP, IPX, and equipment such as routers work
here. This layer doesn’t concern itself with reliability of the data transfer,
since that’s the responsibility of the Transport layer. Its concern is more
along the lines of ‘where am I going (the address), and how do I get there (the
routing).
Data Link Layer – Layer 2 of the OSI Model is concerned with how upper
level data is formatted for transmission over a given network technology. For
example, if your network is running Ethernet, this layer will format the data
accordingly, and follow the rules of Ethernet transmission on the network. Over
the course of being transmitted over a large internetworking, the layer may
change many times between the source and destination – the journey might start
on Ethernet, move over an ATM network, and then end on a Token Ring LAN. The
process of getting across those networks might involve a number of Data Link
layer changes to the packet on even a short trip. This layer is actually made up
of 2 sub-layers, one called the MAC (Media Access Control), which controls
accessing the physical network media, and the other called the LLC (Logical Link
Control), whose responsibility is identifying and interacting with the
upper-level Layer 3 protocol being used. Examples of Data Link protocols include
a variety of network communication standards – Ethernet, Token Ring, FDDI and so
forth. At this layer, systems are generally identified by what is referred to as
their hardware or MAC address.
Physical Layer – Layer 1 of the OSI model is generally the easiest to
identify, because it defines the actual media and characteristics used to send
the 1’s and 0’s over the network. This includes the actual wiring itself, the
connectors used, voltage levels, maximum media distances and so forth. The
physical layer doesn’t change the actual data, although the transmission
mechanism itself can vary greatly over the course of transferring data. For
example, it might start on twisted-pair wiring, move onto a wireless network,
and then ultimately end up on fibre – each of which using different media and
methods during the transfer process. In this case, copper wiring, then air, and
then fibre optic cable.
The Packet Creation Process
So who cares? Good question. The OSI model is all-to-often described without any
perspective of why this stuff is actually important. The answer is simple if you
just take the time to put it all together in a reasonable scenario; it truly
explains what happens when 2 systems actually communicate. The key to
understanding the model is to look at it with respect to how a packet is built
on the source system and then stripped apart at the receiving end. This process
is referred to as data encapsulation.
Data encapsulation is the process by which a packet is built. It all begins
which a chunk of data from the application layer. Maybe you want to view a web
page or send a file over the network to another system. In order to get to that
other system, information will need to be added to the data to account for
reliability, how its going to get to where it needs to go, and the network
technology in use.
When looking at the OSI model, the 7 Layers are often grouped into 2 main
sections. The top section, comprised of the Application, Presentation and
Session Layers, are often referred to as the Application layers, while the
bottom four are often generically referred to as the Transport layers. For the
purpose of looking at the data encapsulation process, the Applications layers
are generally considered to simply pass data, while the Transport layers
actually ‘add’ to the data to help prepare it to make its way across the
network.
Remember that the chunk of data is passed down the layers for formatting. Once
it reaches the transport layer, it makes its first big change, usually in the
form of header and trailer data being added. At each subsequent layer (except
the physical layer, which doesn’t change the packet) more header and trailer
data is added again. This process is referred to as encapsulation, which each
layer literally adding to the packet building process.
A key thing to understand is that as each layer receives the packet and adds to
it, it considers everything passes down to it as simple data. That is, whatever
the transport layer adds is not of concern to the network layer, and so forth.
In that way, each lower layer simply considers what is being passed down to it
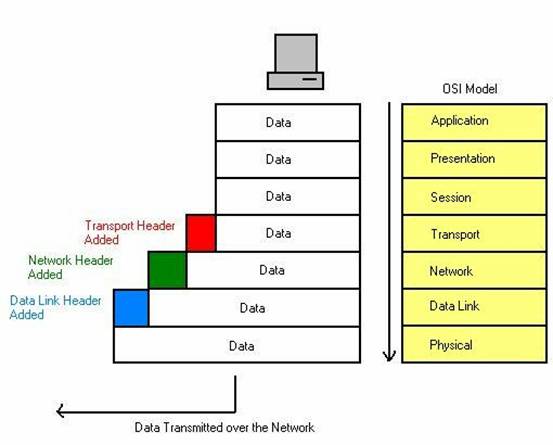
as data. Consider the diagram below, which outlines how each of these layers
changes the data (for clarity purposes, I’ve left off the trailer additions).

What happens above is easily explained, even though the diagram is highly
simplified. Once data is passed to the transport layer, it adds header (and
trailer, not shown) information to the data. If this were a TCP/IP packet, that
would include TCP or UDP source and destination port information. The network
layer would see this all as data, not concerned with what was added. Instead, it
would encapsulate the data with another header, which would involve adding the
source and destination IP addresses. When passed down to the Data Link layer,
still another header would be added – in the case of an Ethernet network, this
would include the source and destination MAC addresses. This would then be
passed to the Physical layer, in the form of binary data being transmitted
across the network.
At the receiving end, the data would subsequently by de-encapsulated, layer by
layer in the opposite direction. For example, the receiving station would
receive the data stream and pass it up to the data link layer.
1. If this station noticed that its MAC address were the destination MAC
address, it would know that it has to pay attention and process the packet,
striping off the data link header and passing it up to the network layer. If
not, it would simply discard the packet at this point.
2. Next, it will pass the packet up to the Network Layer. At this point, it will
determine whether the destination IP address is its IP address. If so, it will
strip off the network header and pass it up to the transport layer. You should
note that just because the MAC address belongs to the system, it doesn’t
necessarily mean that the IP address does as well. For example, a router will
receive many packets with its MAC address and different IP destination
addresses.
3. Once the packet has been passed up to the Transport layer, it is definitely
destined for this system. This layer will take a look at the destination port
listed in the header, strip the header, and then pass the data to the
appropriate application that is waiting for the data, assuming that application
exists (it may not – imaging a request for a web page from a system not running
as a web server)
Note that at each point in the process, a layer only looks at the information
added by its equivalent layer at the sending machine. To that end, the only
layers that a given layer ever interacts with are the equivalent layers on other
systems, as well as the layers directly above and below it on the same system.
The fact that layers are independent of each other is another design goal of the
OSI model - changing a given layer should not effect other layers in the model
One last note with respect to the encapsulation process described above. As each
layer changes the data, the reference name for that data unit is changed.
‘Packet’ is a generic name often used to describe the unit at any stage of the
process. However, the following terms are commonly used to describe data at
different network layers:
Data units above the Transport layer = Messages
Transport layer data units = Segments
Network layer data units = Datagrams or Packets
Data Link layer data units = Frames